Countermeasures against Erebus attacks
Paper: "On the Routing-Aware Peering against Network-Eclipse Attacks in Bitcoin", USENIX Security 2021
TL;DR
We critically analyze Routing-Aware Peering (RAP), a desirable long-term solution to the Erebus attack that incorporates routing information to Bitcoin peer selection.
Unfortunately, we find that Erebus adversaries can still exploit a tiny portion of inevitable route inference errors in any RAP implementations to successfully eclipse Bitcoin nodes.
As a practical suggestion to Bitcoin, we propose an integrated defense framework that composes the available Bitcoin protocol tweaks and the optimal RAP implementation to prevent most Erebus attacks.
Overview
The recent Erebus attack shows that eclipse attacks with network-Sybil capability against Bitcoin's P2P network are possible.
A few Bitcoin protocol tweaks have been quickly implemented to counter the attacks; yet, they are not complete solutions.
This work focuses on a more fundamental solution called Routing-Aware Peering (RAP).
RAP empowers individual Bitcoin nodes to analyze the routes towards their peers and detect Erebus adversaries, e.g., malicious Internet Service Providers (ISPs).
Unfortunately, we discover a critical weakness of RAP approaches, that is, their infrequent yet inevitable route inference errors.
With such inference errors, Erebus adversaries can still create tens or even hundreds of thousands of Sybil peers and successfully eclipse victim Bitcoin nodes in many cases.
To that end, we propose an integrated defense framework that customizes the available simple protocol tweaks and RAP implementation for individual Bitcoin nodes to prevent most of Erebus attacks from the top-100 large ISPs.
Routing-Aware Peering (RAP)
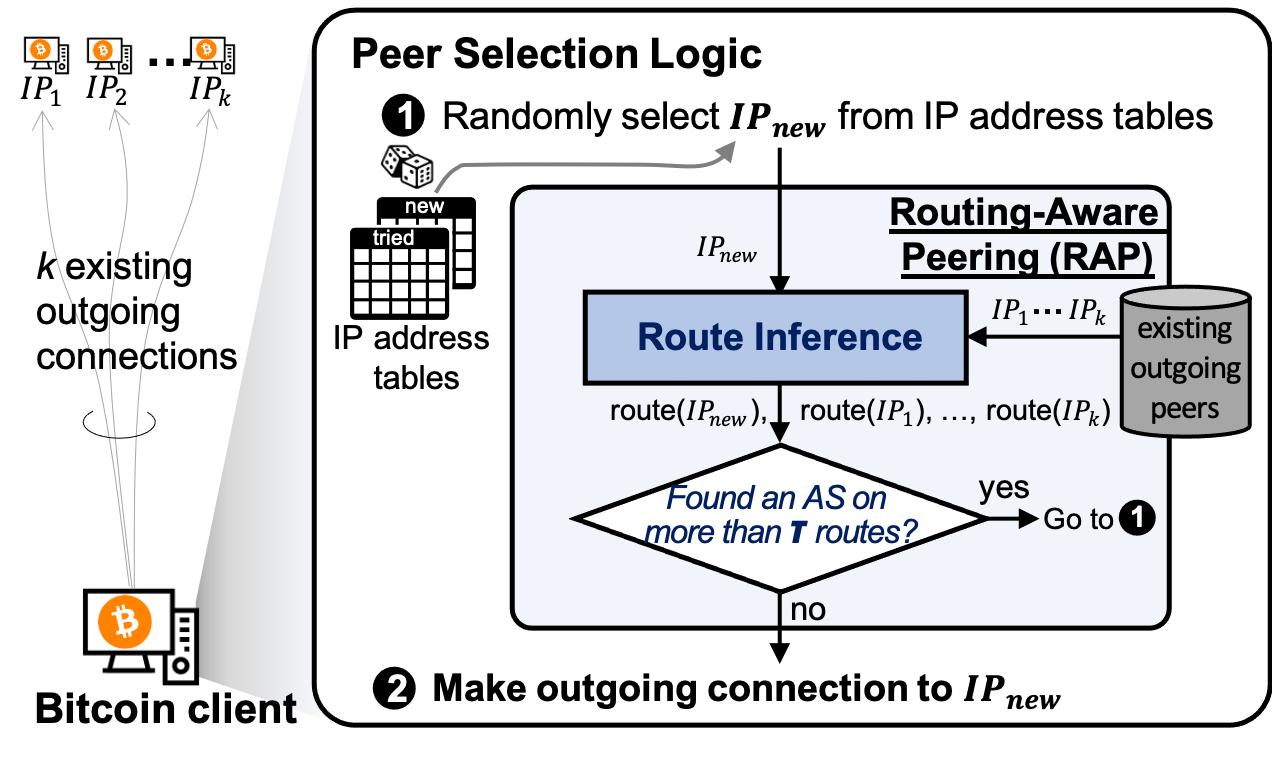
Design overview
RAP adds a test before establishing new connections in Bitcoin. If an AS appears on the inferred route (AS-path) to the new IP as well as (some or all) routes to existing peers, this IP is rejected. The threshold T (1 <= T <= 10) is an adjustable parameter controlling how strictly the RAP function is operated, i.e., the maximum number of allowed outgoing connections that go through an AS.

The Devil is in the detail: Inevitable inference errors
Any route inference approach may misidentify a Sybil peer as considering the route to it does not include the attacker. The adversary can use such misidentified Sybil peers in an Erebus attack to circumvent RAP and eclipse a victim Bitcoin node.
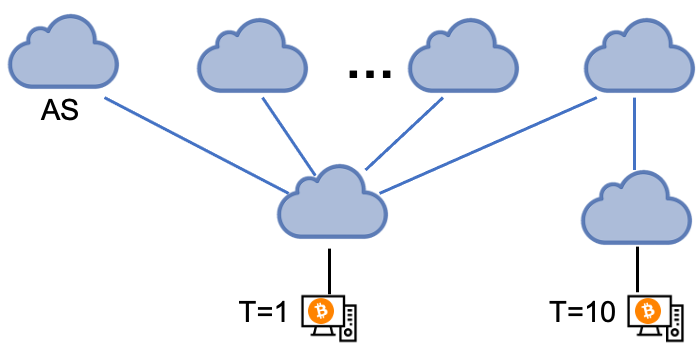
Location-based customization
RAP must be customized for individual Bitcoin nodes based on their locations. For example, nodes in well-connected ASes can enforce disjoint paths by setting low a threshold T. The optimal threshold is a minimum value that ensures all outgoing connections are established.
Main Results
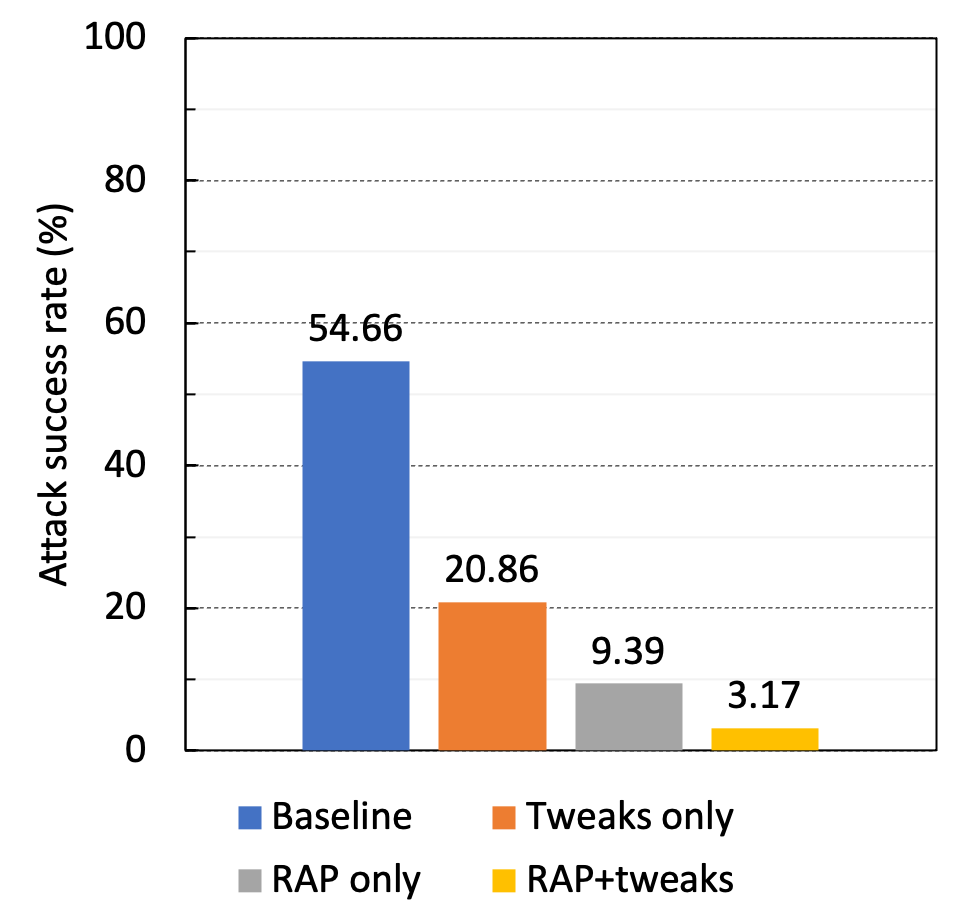
Evaluation is done by emulating ~6,000 scenarios of different attacker-victim pairs. See our extended emulation framework of the Bitcoin network stack for more details.
Tweaks must be carefully combined
We evaluate all possible tweak combinations from 03 new and 03 existing tweaks to find the best combination that reduces the Erebus attack success rate to 20.86%.
RAP alone is insufficient
RAP with optimal customizations reduces the attack success rate to 9.39%. This insufficient defense performance is caused by Erebus attacks using misidentified Sybil peers.
Combining RAP and tweaks
Combining RAP and tweaks makes the most effective countermeasure against the Erebus attacks as the attack success rates drop to 3.17%.
Frequently Asked Questions
About Erebus attacks
[Q1] What is the Erebus attack?
Please refer to the main website of the Erebus attack for more details.
[Q2] What countermeasures have been deployed against the Erebus attack?
As of this writing, three following Bitcoin protocol tweaks have been made to counter the Erebus attack:
(1) AS map,
(2) anchor connections, and
(3) two more outgoing connections.
[Q3] Is there any real-world instance of Erebus attack yet?
We still haven't heard any reports about Erebus attacks on Bitcoin.
However, last years have seen Eclipse attacks against other cryptocurrencies, such as Monero.
About RAP
[Q4] Why is RAP believed to prevent the Erebus attack?
Because RAP provides each Bitcoin node with a defense capability that is symmetric to Erebus adversaries (i.e., end-to-end routing knowledge).
Moreover, the idea of RAP has been already shown to be highly effective in securing Tor against network-based privacy attacks.
[Q5] Why is there always inference error in RAP?
The only way to get the accurate route is via data-plane active measurements (e.g., using traceroute), which cannot be used in practice because the measurement packets traverse through the adversary network and can be easily manipulated.
The available options include local route estimation and querying the routing table of the home network. Both methods return the control-plane routes, which cannot be the same as the data-plane routes, hence the inevitable inference errors.
[Q6] How does an adversary find the misidentified Sybil peers?
The adversary can send a spoofed packet (e.g., TCP SYN) with a source address p to the victim.
If the adversary observes a reply packet (e.g., TCP SYN/ACK), p can be used as a Sybil peer.
Then p is tested with RAP's route inference to see if RAP misidentifies it.
[Q7] Why does RAP work in Tor but not in Bitcoin?
Tor is not a fully permissionless system like Bitcoin as new relays must have their bandwidth reviewed before joining.
Hence, network attackers cannot attack Tor even when RAP in Tor misidentifies large numbers of Sybil identities.
[Q8] Are there any performance overhead?
To enable RAP, Bitcoin nodes may need to pre-compute the routes to other IP addresses locally or query the home network for them regularly (e.g., every month).
Besides that, the performance overhead for establishing new connections is negligible.
[Q9] Does RAP only apply to Bitcoin?
RAP is not Bitcoin-specific and can be applied to the peer establishment of any other cryptocurrencies.
[Q10] What are the differences between RAP and existing quick defenses (e.g., relays, Tor, VPNs)?
RAP does not hurt the openness and decentralization of Bitcoin.
About Bitcoin tweaks
[Q11] How are Bitcoin tweaks systematically found?
We list all possible steps of the life-cycle of an IP address in the internal data structure of Bitcoin.
By doing so, we find 03 new protocol tweaks in addition to the existing ones.
[Q12] Why don't we simply combine all possible tweaks?
Because the efficacy of these countermeasures is non-monotonic --- activating more countermeasures does not necessarily guarantee higher defense performance in terms of attack success rate. Thus, we need to evaluate many combinations and select a proper set of countermeasures.
[Q13] Is there a performance evaluation of individual tweaks?
Yes, please refer to our paper.
[Q14] Can similar tweaks work for other cryptocurrencies?
Yes if the other cryptocurrency has a similar P2P code as Bitcoin, see a few examples on the Erebus attack website.
They can also potentially be applied to other cryptocurrencies that have similar peer management data structures at a high-level, such as Etherum and Monero.
Others
[Q15] What to do if I am running a Bitcoin node?
You should wait for Bitcoin Core updates, as RAP and other protocol tweaks are being considered by Bitcoin Core developers.
[Q16] Should I consider multi-homed ISPs to host my Bitcoin node?
Yes, it helps to reduce the risk of naturally having a common ISP on your connections and when RAP is deployed.
However, it does not help if a malicious large ISP actively launching Erebus attacks against your node.
People
© Muoi Tran. Design: Surjith S M. Last update on March 1, 2021.



